Denial of Service and the xISP Part 1
Most service providers have been the victim of a Denial of Service (DoS) attack at one point or another. Sometimes you may not realize you are under an attack. A few months ago, I posted a simple screenshot at https://blog.j2sw.com/networking/anatomy-of-a-ddos/ of what an active DDoS looks like.

Types of Attacks
In order to know what to look for you have to understand the four basic types of attacks. I will outline this and talk about how modern attacks are affecting Internet Service Providers (ISPs). In my next article, we will talk about identifying these types of attacks and some mitigation techniques you can employ.
Throw everything at you attack aka Buffer overflow
This type of attack is throwing enormous amounts of traffic at you to fill up your switch and router buffers, causing the device to exceed its capabilities. Your devices become crushed by an overwhelming volume of data throw at them. This attack isn’t always sheer bandwidth. Sometimes it is tens of thousands of remote connections.
Attacking vulnerable protocols
Attackers go after exposed services like ICMP to do amplification attacks. Fragmented packets, which keep the router tied up are also a common method of attacking a host.
Application attacks
These are the ones most consumers hear about. Vulnerabilities in operating systems, applications, and packages are exploited and used in attacks.
Hacks
The fourth kind is not lumped in with Application attacks, but I wanted to separate it for a few reasons. The first reason is that someone compromising a system is not always sophisticated. If a bad actor guessed the password on your router and erased the configuration, they have performed a Denial of Service against you. If you don’t keep your software up-to-date and someone exploits a backdoor and “hacks” your system, they have performed of DoS attack.

Modern Attacks against networks
Modern DoS attacks are always evolving. As network administrators find ways to mitigate these attacks, the bad actors find ways to tweak them and get around mitigation techniques employed by providers. Most of the exploits above involve sheer volumes of traffic or connections being directed at a host to take it offline. This attack is especially detrimental for service providers because it takes your customers offline if the attack is significant enough.
One of the most common techniques these days is the Distributed Denial of Service attack (DDoS). These are usually botnets involving thousands of compromised machines or devices acting against a host(s). These can be anywhere in the world. They could even be users inside your network with compromised machines or other devices. Distributed attacks are hard to mitigate because they can be legitimate traffic pointed at a web-server as an example. The traffic is not malicious from a technical perspective. You have thousands and thousands of machines sending legitimate requests to a web-server or other host on your network. This traffic looks legitimate but is overwhelming for your hardware and Internet pipe.
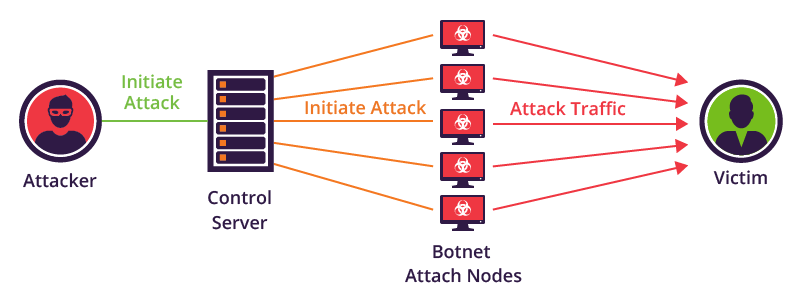
So what does a DDoS look like and what are your options when it comes to Denial of Service Attacks? In my next article in this series, I will talk about some best practices you can do so you are not as vulnerable to these types of attacks.
j2networks family of siteshttps://j2sw.com
https://startawisp.info
https://indycolo.net
#packetsdownrange #routethelight